Automated Remediation
Table of Contents
Table of Contents
Go beyond basic analysis and let AI Agents diagnose failures, propose fixes, and open pull requests automatically.
The problem
Finding the root cause of a test failure is only half the battle. Once you know what's broken, you still have to fix it.
That means switching context from your test platform to your IDE, pulling down the latest code, making the change, creating a branch, writing a commit message, and opening a pull request. For a simple bug, this takes 10 to 15 minutes. For something more complex or unfamiliar code, it can stretch past 30 minutes.
Multiply this across a team handling dozens of failures per week and remediation becomes a significant time sink. Worse, the delay between identifying a problem and shipping a fix creates risk. Broken tests block pipelines, slow releases, and erode confidence in your test suite.
The manual handoff from "I know what's wrong" to "it's fixed" is where momentum dies.
The solution
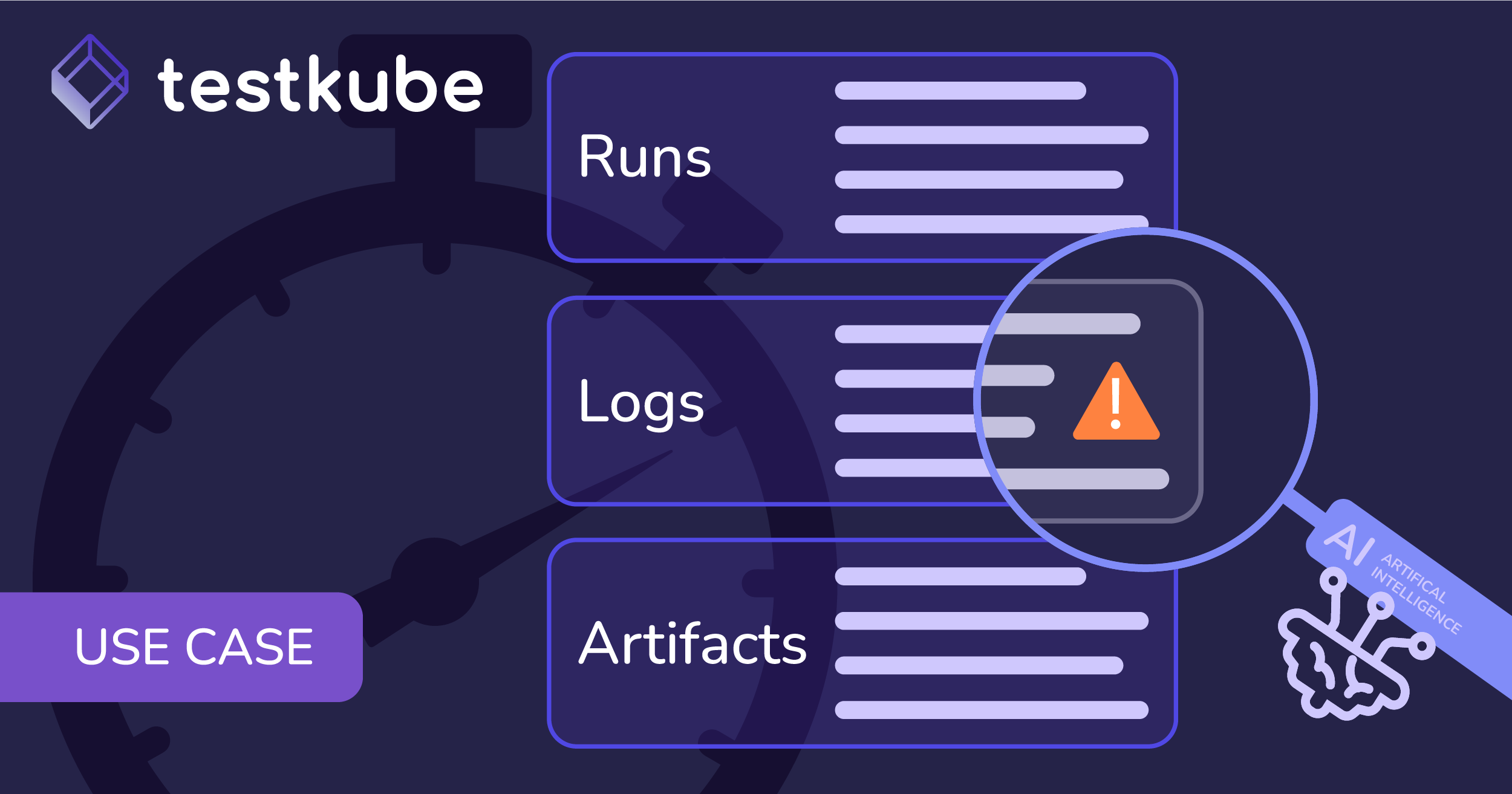
Testkube's AI Agent Framework enables agents that don't just analyze failures—they act on them. A remediation agent examines test logs, identifies the root cause, correlates with recent code changes, generates a fix, and opens a pull request in your repository. All without leaving Testkube.
This closes the loop between detection and resolution. Instead of copying error messages into your IDE, you get a ready-to-review PR with a clear explanation of what was wrong and how the agent attempted to fix it.
How it works
Testkube remediation agents combine two MCP server connections: the Testkube MCP Server for test execution data, and a GitHub or GitLab MCP Server for repository access.
Testkube MCP Server provides test context: The Testkube MCP Server gives agents access to execution logs, artifacts, failure details, and workflow metadata—everything needed to understand why a test failed, not just that it failed.
Connect your source control MCP server: Add the GitHub or GitLab MCP Server with a scoped access token. The agent needs permission to list recent commits, create branches, commit files, and open pull requests. It cannot delete files or merge code. Testkube can associate workflows with repositories through workflow annotations, git configuration, or other methods—so the agent knows where to target its fix.
Trigger remediation from a failed execution: Navigate to a failed workflow execution and click AI Analyze. Select your remediation agent and run it. The agent investigates logs and artifacts, examines recent commits, identifies the root cause, and opens a pull request with its analysis and proposed fix.
Review and merge: The agent doesn't merge anything on its own. It proposes a fix, explains its reasoning, and hands it off to your team. Merge, refine, or reject based on your review. Humans stay in control.
Key capabilities
- Analyze failed test logs and artifacts to identify root cause
- Inspect recent commits in connected repositories to correlate failures with code changes
- Generate a proposed fix based on analysis
- Create a new branch and commit the fix automatically
- Open a pull request with a description of the issue and remediation approach
- Optionally notify teams via Slack or create tracking issues in Jira
Outcomes
- Cut remediation time from 30+ minutes to under 5 for common failures
- Reduce context switching by staying in Testkube instead of jumping between tools
- Accelerate release cycles by closing the gap between detection and fix
- Keep humans in control with review-ready PRs, not auto-merged changes
Built-in guardrails
Giving an AI agent access to your codebase sounds risky. Testkube builds in controls to keep agents scoped and safe.
Scoped permissions. When connecting MCP servers with your AI Agents, you choose exactly which tools an agent can access. A remediation agent can create branches and open PRs, but not delete files or merge code.
Token-based access. GitHub and GitLab tokens can be scoped to specific repositories and actions. You control what the agent can touch.
Human-in-the-loop. Agents propose changes via pull requests. Your team reviews and merges—or doesn't. Nothing ships without approval.
Tool approval prompts. For sensitive actions, Testkube can require manual approval before the agent proceeds. You see what it's about to do before it does it.
What makes this different
Generic AI coding assistants can suggest fixes, but they're working blind. They don't have access to your test execution data, failure history, or environment context—only the error message you paste in.
Testkube remediation agents start from the test failure itself. They see the logs, the artifacts, the execution history, and correlate that with your source code and recent commits. The result is fixes grounded in what actually went wrong.



.png)