Table of Contents
Try Testkube instantly in our sandbox. No setup needed.
Try Testkube instantly in our sandbox. No setup needed.


Table of Contents
Executive Summary
Kubernetes promises to simplify and supercharge your container orchestration, but it introduces a sprawling attack surface that is a nightmare for administrators. API servers, etcd, clusters, pod-to-pod communication, RBAC, admission controllers, and network policies each add their own complexity.
Traditional security testing practices were not designed to handle the complexities that Kubernetes introduces. In fact, 67% of organizations have delayed app deployment due to security concerns. The promise of agility and flexibility is meaningless if security vulnerabilities force you to choose between speed and safety.
The idea isn’t abandoning Kubernetes or accepting security as an afterthought; rather, it’s about implementing a structure, repeatable security testing framework that integrates seamlessly with your existing workflows.
In this article, we’ll explore essential components, tools, and implementation strategies for implementing a comprehensive Kubernetes security testing framework that helps your organization maintain agility and a robust security posture.
What is a Kubernetes Security Testing Framework?
Traditional approaches treat applications and infrastructure as two separate concerns. They scan code for vulnerabilities, harden servers with security policies, and monitor networks for intrusions. But the dynamics change completely with Kubernetes. Your application configuration defines how your infrastructure behaves, your infrastructure policies control how your application is accessed, and finally, your runtime affects both.
A Kubernetes security testing framework is a collection of automated tools, policies, and processes designed specifically for cloud-native environments where infrastructure is code, workloads are temporary, and the attack surface is constantly changing.
Unlike traditional security testing, which focuses on application code vulnerability or infrastructure only, this framework treats security as a continuous, automated workflow integrated with your CI/CD workflows.
Key Components of a Kubernetes Security Testing Framework
Pre-deployment Scanning
Misconfigurations remain a significant concern, and catching them early prevents issues in production. A single configuration error like runAsUser: 0 can grant root access to every container in your deployment, which can be catastrophic.
Pre-deployment scanning enables automated validation of your Kubernetes manifests, Helm charts, and configurations before they reach your cluster. Tools like kube-linter scan your YAML files for best practices violations while OPA Gatekeeper enforces custom policies like “no containers running as root”.
For example, your team pushes a new microservice deployment. Pre-deployment scanning automatically catches that the service account has cluster-admin role (excessive permissions), doesn’t define resource limits for the container (potential resource hog), and uses the latest image tag. The deployment is instance blocked with actionable feedback.
Image Scanning
Using images from untrusted sources for your containerized application is a recipe for disaster. Many container images contain outdated libraries with known CVEs. This allows malicious actors to compromise your environments.
Automated image scanning is integrated into your CI/CD pipeline. It checks for vulnerabilities in container images and their dependencies and reports them before deployment. Tools like Trivy provide a comprehensive scan with Software Bill of Materials (SBOM) generation, while Grype can scan and detect vulnerabilities across different package types.
For instance, a developer updates a Python app using an older logging library version. Image scanning during the CI build detects a CVE in the library, automatically fails the build, and suggests the developer update to a newer version that patches the vulnerability.
Runtime Security Testing
While static analysis helps detect specific vulnerabilities, it can’t detect zero-day exploits or behavioural anomalies. Without any runtime security testing, your system cannot actively detect threats.
Runtime security testing refers to the continuous monitoring of live Kubernetes workloads in real time to detect suspicious activity, unauthorized access attempts, or policy violations. Tools like Falco monitor system calls and Kubernetes events in real time to detect anomalies, while Sysdig provides behavioral analytics helpful for debugging incident response.
Imagine a compromised container deployed in production starting to make network calls to external IPs and attempting to read files from other pods. Tools like Falco can detect these, trigger an alert, and automatically quarantine the pod while generating detailed logs for the security team.
Configuration & Secret Management Validation
One of the common security concerns is improper credential management. Developers often accidentally expose credentials in configuration, leading to attacks. Even overly permissive RBAC policies are entry points for lateral movement attacks within your environment.
Thus, to prevent data exposure or privilege escalation, automated detection of hardcoded secrets, weak RBAC configurations, and excessive permissions is required. Tools like Gitleaks can scan code repositories for exposed API keys, passwords, and tokens, while rbac-lookup can help analyze Kubernetes RBAC configurations to find overprivileged service accounts.
This is helpful when, during a routing scan, the framework detects that a microservice’s service account has permission across all namespaces even though it needed only read access to its own config. Issues like these can be flagged immediately for remediation.
Network & Pod Security Testing
If proper network isolation is not configured, a single compromised pod can access any other service, pod, or filesystem in large-scale deployments. In addition, many organizations have workloads that are impacted by containers that are permitted to run in privileged mode.
Hence, network policies, pod security standards, and inter-service communication rules must be validated to ensure proper segmentation and fine-grained access control. Tools like Cilium provide network policy testing and observability, while Pod Security Standards ensure pods run with the minimal required privileges.
For example, a new deployment lacks network policies, which allows its pods to communicate with any service, including the payment processing system. Network security testing can identify this gap and suggest implementing policies that only allow communication with the authenticated service while blocking access to other sensitive services.
Compliance & Benchmarking
Whether handling people’s health records or storing credit card details, compliance has become a fundamental requirement for many organizations. It isn’t a one-time activity, but requires periodic audits. Further, manual compliance checks are error-prone and can’t keep up with the dynamic environment.
Continuous compliance monitoring ensures automated assessment against industry frameworks like CIS Kubernetes benchmarks, SOC2, or other organizational policies. Tools like kube-bench can automatically validate cluster configuration against CIS Kubernetes benchmarks, while Kubescape can perform multi-framework compliance testing, including MITRE, NSA, etc., guidelines and frameworks.
Instead of manually gathering your quarterly compliance reports, you execute weekly automated benchmarking runs that show any deviations and suggest remediation steps for each finding.
Framework Example: Putting It All Together
At this point, we have understood the individual security components; however, it is critical to understand how they work together as a comprehensive system. Let’s look at a microservice deployment scenario to see how these tools work together.
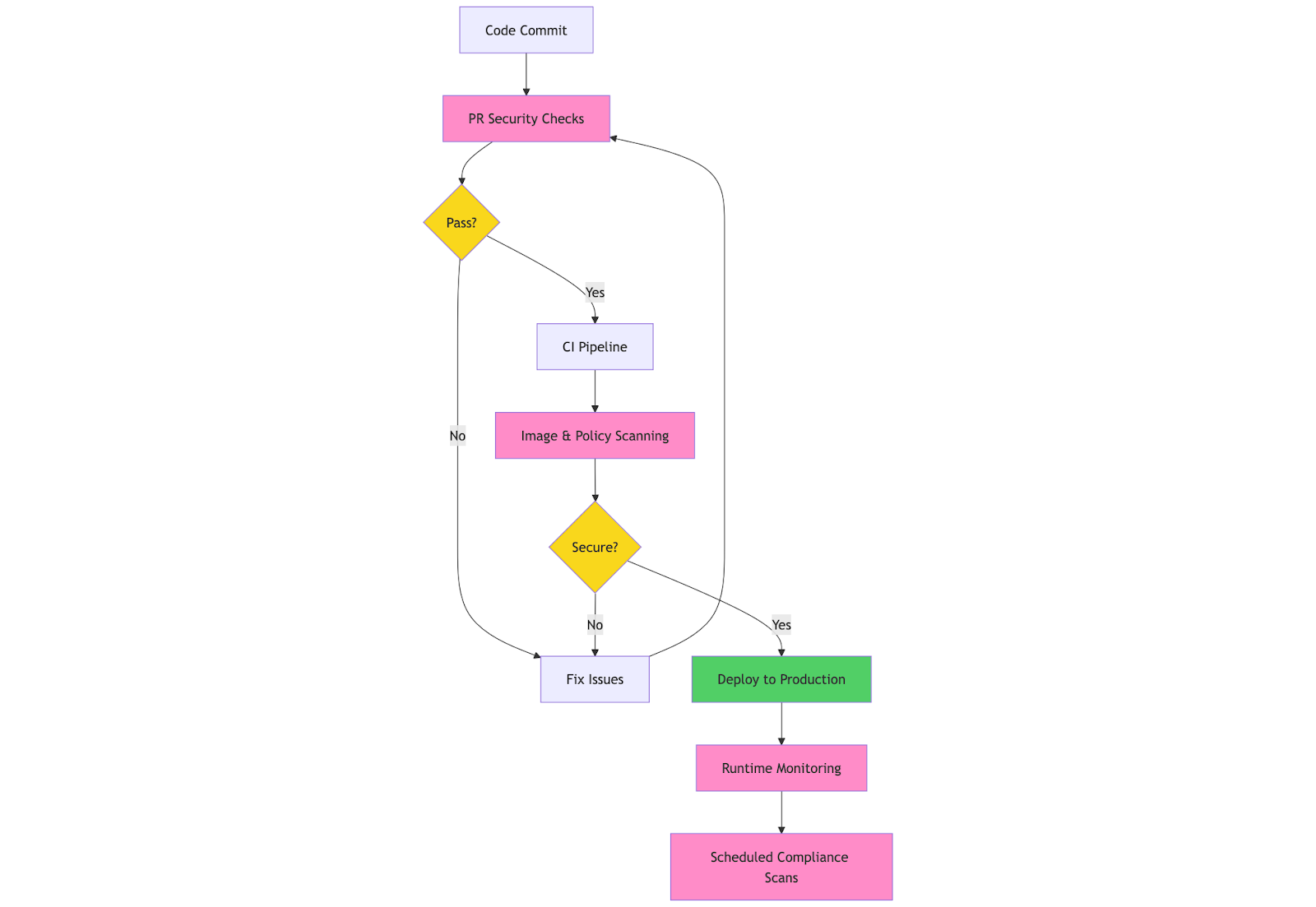
A developer deploys a new payment microservice that handles sensitive customer data. Here’s how the Kubernetes security framework guides the process:
- PR Creation: When the code is pushed to the repository, GitLeaks scans for secrets, kube-linter validates the YAML configurations, and OPA policies check service account privileges. The PR is blocked until the hardcoded database password is removed.
- CI Pipeline: Trivy detects a critical vulnerability in a JSON parsing library, OPA validates that network policies restrict communication to only authentication and payment services. The build will fail until the vulnerable library is patched.
- Staging Deployment: Falco begins monitoring system calls and establishes behavioural baselines for normal payment processing patterns.
- Production with Runtime Monitoring: Falco detects suspicious activities, such as unexpected outbound connections, and is ready to quarantine such pods with an automated incident response system in place.
- Continuous Compliance: Kube-bench runs CIS benchmark tests weekly, an RBAC audit verifies least-privilege principles, and compliance reports automatically document security postures for SOC2 audits.
How Testkube Can Help Orchestrate Security Testing in Kubernetes
In the previous section, we saw how various security tools can work in a workflow to provide comprehensive security. While these tools are powerful, orchestrating them effectively in dynamic Kubernetes environments requires a different approach. This is where Testkube comes in with extended capabilities for security testing, providing automated testing, integrated security checks into CI/CD pipelines, and simplified troubleshooting.
Let us look at how Testkube can help orchestrate security testing in Kubernetes.
Native Kubernetes Test Orchestration
Testkube “converts” your existing testing tools into Kubernetes native so they can leverage the full benefits of Kubernetes without needing you to do complex configuration changes. Whether you’re using OWASP Zap for vulnerability testing or Trivy for image scanning, Testkube treats each as a native test type within your cluster. This eliminates the overhead of external testing infrastructure while providing a seamless and consistent test execution across environments.
Read more about using Testkube for security testing in Kubernetes.
Automated Policy and Workflow Management
As part of your security testing plan, you can check for vulnerabilities or loopholes in your applications, validate access permissions, and take corrective action to harden them. Testkube test workflows can automatically trigger kube-bench compliance scans and coordinate multi-tool security assessments without manual intervention.
Read more about different types of testing in Kubernetes.
Centralized Results and Flexible Triggers
Testkube has its own set of CRDs that interact with Kubernetes components, allowing it to fully utilize Kubernetes for efficient testing. Testkube can aggregate test results and summaries from multiple tools into a unified dashboard. Further, tests can be triggered via API calls, CLI commands, GitOps events, or scheduled intervals, thus providing the flexibility of both automated and manual security validation.
Read more about all supported test workflow triggers.
Seamless CI/CD integration
Testkube seamlessly integrates into your existing CI/CD and/or GitOps workflows without you performing complex configuration changes. Testkube supports a variety of testing tools that you can configure as part of your workflow - trivy for image scanning, Postman for API testing, k6 for load testing - and all of these are orchestrated as part of your deployment process.
Read more about testing in CI/CD and GitOps.
Challenges and Best Practices
Implementing a Kubernetes security framework requires a good understanding of your existing security posture, infrastructure, and applications. Let's look at some challenges and best practices that you can follow.
Challenges
- Security Checkpoint Mindset: Many organizations treat security as a checkpoint or final gate and delay their deployments until the goal is met. Instead, teams must implement security at every stage - from pre-commit hooks, PR validation, CI scanning, and runtime - making security a continuous process.
- Runtime Blind Spots: Teams focus on static analysis while missing attack attempts after deploying the application. They should deploy runtime tools like Falco alongside static scanning and create behavioural baselines and automated incident response workflows.
- Overpermissioning: Accidental exposure of credentials in configuration files and service accounts is a potential attack vector. Teams must follow zero-trust principles and provide the least permissions, ensure that you have automated RBAC auditing, and perform regular permissions reviews with tools like rbac-lookup.
- Velocity vs. Security Trade-off: Teams believe that security scanning slows CI/CD pipelines, creating pressure to bypass checks and ship features faster. Instead, teams must optimize scan performance, implement parallel security testing, and provide faster feedback loops.
Best Practices
- Automate Everything: Automate your security checks as much as possible, including policy validation, compliance as code, and vulnerability monitoring.
- Foster Cross-team Collaboration: Integrate the processes and tools to ensure that security is a shared responsibility between the DevOps and security teams.
- Faster and Continuous Feedback: Provide fast, immediate, and actionable feedback with dashboards showing the security trends and use AI-powered tools to suggest improvements.
- Progressive Security Hardening: Start by fixing basic security configurations, implement risk-based prioritization for public-facing workloads, and, as the organization matures, create and implement compliance frameworks and policies.
Conclusion
Kubernetes security testing frameworks help teams implement security best practices at every stage - from code commit to runtime monitoring. With organizations losing revenue due to security incidents, the shift from reactive security checks to proactive testing is a strategic move.
Thus, evaluate your existing security posture and understand your security coverage. Are you only scanning in CI? Are you missing runtime threats? The gap between your current security and desired state is a risk and an opportunity.
Ready to get started? Try Testkube to orchestrate your security tests and transform your security testing into a competitive advantage.


About Testkube
Testkube is a cloud-native continuous testing platform for Kubernetes. It runs tests directly in your clusters, works with any CI/CD system, and supports every testing tool your team uses. By removing CI/CD bottlenecks, Testkube helps teams ship faster with confidence.
Explore the sandbox to see Testkube in action.



.webp)